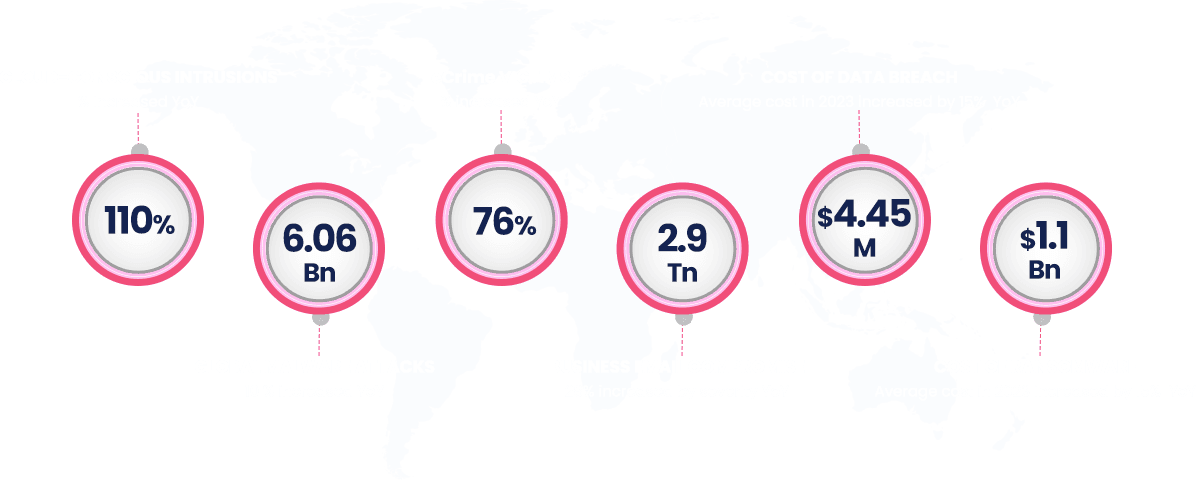
Global overview of Cyber Threats
Cyber Attacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users via ransomware; or interrupting normal business processes
to analyse your current IT security risks and select appropriate data protection product & plan to safeguard your critical business information
Once purchased, our team of certified professionals help you analyse & prepare a robust Data Protection Policy to get you started. We help install agent, configure backup, enable security & notifications
Once operational, we perform daily malware scans, real-time monitoring, risk mitigations and alert fixes. In addition as per plan we also deliver monthly vulnerability assessments, cyber forensics assistance & recovery on demand
Managed Service includes:
Need Help?
Agentless Backup & Recovery with unlimited cloud storage for Exchange, OneDrive, SharePoint, Contacts and Calendar with Advanced Email & Collaboration Apps Security

Loading...
Want to reduce license costs?
Move your non-power users to POP3/IMAP Business Email without changing domain
GET Hybrid Email Solution>Backup your data from Microsoft/Google data centers directly. Ensure compliance, quickly recover all the data you need with greatly improved RTO (recovery time objective)
Protect emails, attachments, contacts, tasks, group mailboxes, archive mailboxes and calendars ensuring business continuity and compliance
Quick access with metadata and full text search to restore files or entire folders with previous sharing permission
Block malicious communications leveraging the combined data of several market-leading technologies
Detect malicious hidden content by recursively unpacking the content into smaller units (files and URLs) which are then dynamically checked by multiple engines in under 30 seconds
Stay ahead of emerging threats with the combined threat intelligence of six market-leading sources and a unique engine that scans URLs and files in the wild
Identify known threats with best-ofbreed signature-based antivirus engines enhanced with a unique tool to identify highly complex signatures
Detect malicious URLs based on four leading URL reputation engines in combination with an advanced image recognition technology to validate the legitimacy of URLs
Prevent payload-less attacks such as spoofing, look-alike domains, and display name deception with unmatched precision through machine-learning algorithms with IP reputation, SPF, DKIM, and DMARC record checks
Stop advanced attacks such as APTs and zero-days with Perception Point’s unique, CPU-level analysis that detects and blocks them at the exploit stage by identifying deviations from normal execution flow during runtime
Gain direct access to cyber analysts who act as an extension of your service delivery team. Monitors all customer traffic and analyze malicious intent with ongoing reporting and support, including handling false positives, remediating, and releasing when required
Reduce reputational risks for clients and enhance protection accuracy by detecting malicious emails originating from their mailboxes via Microsoft 365 API-based scanning
Added security for SharePoint, OneDrive and other Microsoft 365 cloud collaboration applications
In today's digital age, data is one of the most valuable assets for individuals and organizations alike. Ensuring its safety through effective backup and security measures is paramount. This guide will provide you with a comprehensive overview of cloud data backup and security , offering practical tips and insights to safeguard your data.
Cloud data backup refers to the process of copying data to a remote, cloud-based server for storage and protection. This ensures that data is preserved and can be recovered in case of data loss events such as hardware failures, natural disasters, or cyberattacks.
Evaluate the volume, sensitivity, and criticality of your data to determine appropriate backup strategies and frequencies.
Consider factors such as:
Define how often backups should be performed and how long they should be retained. Balance between storage costs and the need for historical data availability.
Protecting cloud-stored data from unauthorized access, breaches, and other threats is crucial to maintain confidentiality, integrity, and availability.
Familiarize yourself with regulations such as GDPR, HIPAA, and CCPA that govern data protection and privacy.
Adopt standards such as ISO/IEC 27001 for information security management.
Ensure your cloud backup and security practices align with regulatory requirements to avoid legal and financial penalties.
A disaster recovery plan ensures business operations can continue with minimal disruption in the event of data loss or system failure.
Leverage cloud backups to quickly restore critical data and systems as part of your disaster recovery strategy.
Regularly test your disaster recovery plan and update it to address new risks and changes in your business environment.
AI and ML can predict potential security threats and automate responses, improving overall data protection.
Expect increased emphasis on data privacy, more sophisticated encryption methods, and broader adoption of AI-driven security solutions.
Cloud data backup and security are essential components of modern data management strategies. They offer scalability, reliability, and cost-effectiveness, but require careful planning and execution.
By following the guidelines and best practices outlined in this guide, you can effectively safeguard your data in the digital age
In today's digital age, email is the backbone of business communication. It serves as the primary channel for exchanging information, making decisions, and maintaining records. Given its crucial role, safeguarding email communication through robust backup and security measures is essential. This article explores why email backup and security are vital for your business and provides practical steps to implement them effectively.
Emails contain sensitive information, including contracts, financial data, personal information, and strategic plans. The loss or compromise of such data can lead to severe consequences, such as financial loss, reputational damage, and legal repercussions. Here are key reasons why securing and backing up email communication is critical:
To ensure the security and availability of email data, businesses should implement comprehensive email backup solutions. Here are key steps to consider:
In addition to backups, robust security measures are crucial to protect email communications from cyber threats. Here are essential security practices:
In the digital landscape where email is indispensable for business operations, implementing robust email backup and security measures is not just a best practice but a necessity. By ensuring that emails are backed up regularly, encrypted, and protected against cyber threats, businesses can safeguard their critical communication channels, comply with legal requirements, and maintain continuity even in the face of disasters. Investing in email security and backup solutions is an investment in the longevity and integrity of your business.