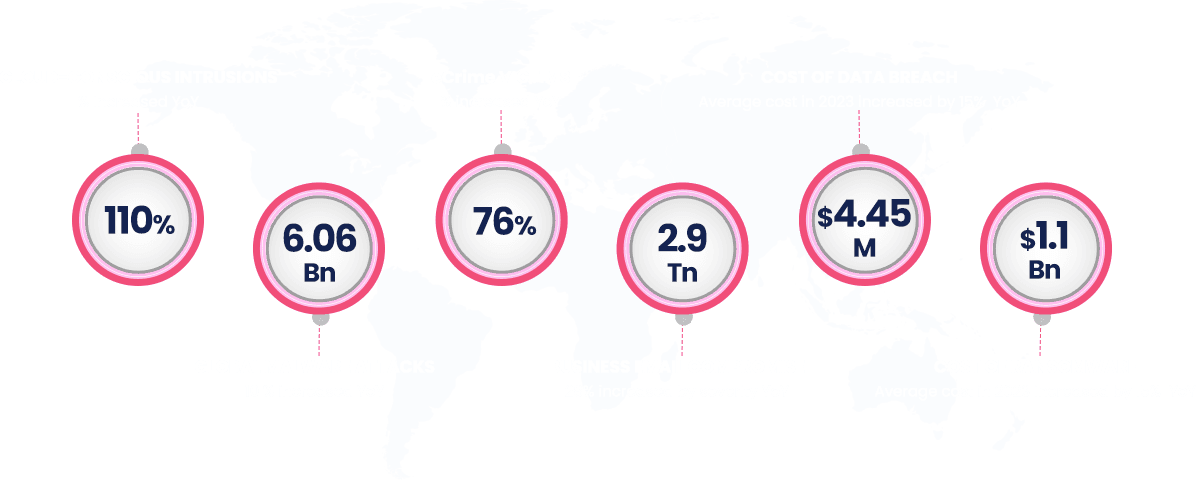
The Ultimate Guide to Cloud Data Backup and Security: Safeguarding Your Data in the Digital Age
In today's digital age, data is one of the most valuable assets for individuals and organizations alike. Ensuring its safety through effective backup and security measures is paramount. This guide will provide you with a comprehensive overview of cloud data backup and security , offering practical tips and insights to safeguard your data.
Table of Contents
- Introduction to Cloud Data Backup
- What is Cloud Data Backup?
- Benefits of Cloud Data Backup
- Types of Cloud Data Backup
- Key Considerations for Cloud Data Backup
- Assessing Data Backup Needs
- Choosing a Cloud Backup Service Provider
- Understanding Backup Frequency and Retention Policies
- Cloud Data Security Essentials
- Importance of Data Security in the Cloud
- Common Threats to Cloud Data
- Best Practices for Cloud Data Security
- Implementing Cloud Data Backup
- Setting Up Cloud Backups
- Automated vs. Manual Backups
- Monitoring and Testing Backups
- Enhancing Cloud Data Security
- Encryption Techniques
- Access Controls and Authentication
- Regular Security Audits and Updates
- Regulatory and Compliance Considerations
- Understanding Data Protection Regulations
- Ensuring Compliance with Industry Standards
- Impact of Regulations on Cloud Backup and Security
- Disaster Recovery and Business Continuity
- Importance of a Disaster Recovery Plan
- Integrating Cloud Backup with Disaster Recovery
- Testing and Updating Disaster Recovery Plans
- Future Trends in Cloud Data Backup and Security
- Emerging Technologies and Practices
- The Role of Artificial Intelligence and Machine Learning
- Predictions for the Future of Cloud Data Protection
- Conclusion
- Recap of Key Points
- Final Recommendations
- Resources for Further Reading
1. Introduction to Cloud Data Backup
What is Cloud Data Backup?
Cloud data backup refers to the process of copying data to a remote, cloud-based server for storage and protection. This ensures that data is preserved and can be recovered in case of data loss events such as hardware failures, natural disasters, or cyberattacks.
Benefits of Cloud Data Backup
- Scalability: Easily scale storage capacity to meet growing data needs.
- Cost-Effectiveness: Reduce the need for physical storage hardware and associated maintenance costs.
- Accessibility: Access data from anywhere with an internet connection.
- Reliability: Benefit from high uptime and redundancy provided by cloud service providers.
Types of Cloud Data Backup
- Full Backup: A complete copy of all data.
- Incremental Backup: Only backs up data that has changed since the last backup.
- Differential Backup: Backs up data that has changed since the last full backup.
- Mirror Backup: A real-time replication of data, often used for immediate recovery.
Key Considerations for Cloud Data Backup
Assessing Data Backup Needs
Evaluate the volume, sensitivity, and criticality of your data to determine appropriate backup strategies and frequencies.
Choosing a Cloud Backup Service Provider
Consider factors such as:
- Reputation and Reliability: Look for providers with a proven track record.
- Security Features: Ensure robust encryption and access controls.
- Support and Service Level Agreements (SLAs): Review the support options and SLAs provided.
Understanding Backup Frequency and Retention Policies
Define how often backups should be performed and how long they should be retained. Balance between storage costs and the need for historical data availability.
3. Cloud Data Security Essentials
Importance of Data Security in the Cloud
Protecting cloud-stored data from unauthorized access, breaches, and other threats is crucial to maintain confidentiality, integrity, and availability.
Common Threats to Cloud Data
- Cyberattacks: Malware, ransomware, and phishing attacks targeting data.
- Insider Threats: Unauthorized access or misuse by employees or contractors.
- Data Loss: Accidental deletions or corruption of data.
Best Practices for Cloud Data Security
- Data Encryption: Encrypt data both in transit and at rest.
- Access Controls: Implement strict access controls and multi-factor authentication.
- Regular Security Audits: Conduct frequent security assessments and audits.
4. Implementing Cloud Data Backup
Setting Up Cloud Backups
- Select Backup Software: Choose software that integrates well with your existing systems.
- Configure Backup Settings: Define what data to back up, schedule backups, and set retention policies.
- Initial Backup: Perform the first full backup to establish a baseline.
Automated vs. Manual Backups
- Automated Backups: Ensure regular, consistent backups without human intervention.
- Manual Backups: Allow for flexibility and control, useful for specific, non-routine backups.
Monitoring and Testing Backups
- Monitoring: Regularly check backup logs and reports for any issues.
- Testing: Periodically test backup restoration processes to ensure data can be successfully recovered.
5. Enhancing Cloud Data Security
Encryption Techniques
- AES (Advanced Encryption Standard): Commonly used for encrypting data.
- End-to-End Encryption: Ensures data is encrypted from the source to the destination.
Access Controls and Authentication
- Role-Based Access Control (RBAC): Restrict access based on user roles.
- Multi-Factor Authentication (MFA): Add an extra layer of security beyond passwords.
Regular Security Audits and Updates
- Security Audits: Regularly review security measures and policies.
- Software Updates: Keep all software and systems up-to-date with the latest security patches.
6. Regulatory and Compliance Considerations
Understanding Data Protection Regulations
Familiarize yourself with regulations such as GDPR, HIPAA, and CCPA that govern data protection and privacy.
Ensuring Compliance with Industry Standards
Adopt standards such as ISO/IEC 27001 for information security management.
Impact of Regulations on Cloud Backup and Security
Ensure your cloud backup and security practices align with regulatory requirements to avoid legal and financial penalties.
7. Disaster Recovery and Business Continuity
Importance of a Disaster Recovery Plan
A disaster recovery plan ensures business operations can continue with minimal disruption in the event of data loss or system failure.
Integrating Cloud Backup with Disaster Recovery
Leverage cloud backups to quickly restore critical data and systems as part of your disaster recovery strategy.
Testing and Updating Disaster Recovery Plans
Regularly test your disaster recovery plan and update it to address new risks and changes in your business environment.
8. Future Trends in Cloud Data Backup and Security
Emerging Technologies and Practices
- Blockchain: Enhances data integrity and security.
- Zero-Trust Security Models: Assume no trust and verify every access request.
The Role of Artificial Intelligence and Machine Learning
AI and ML can predict potential security threats and automate responses, improving overall data protection.
Predictions for the Future of Cloud Data Protection
Expect increased emphasis on data privacy, more sophisticated encryption methods, and broader adoption of AI-driven security solutions.
9. Conclusion
Recap of Key Points
Cloud data backup and security are essential components of modern data management strategies. They offer scalability, reliability, and cost-effectiveness, but require careful planning and execution.
Final Recommendations
- Choose reputable cloud service providers.
- Implement robust security measures.
- Regularly test your backup and disaster recovery plans.
- Stay informed about emerging trends and technologies.
Resources for Further Reading
- NIST Cybersecurity Framework
- ISO/IEC 27001 Information Security Management
- Cloud Security Alliance (CSA) Guidance
By following the guidelines and best practices outlined in this guide, you can effectively safeguard your data in the digital age
Secure Your Business Communication: The Importance of Email Backup and Security
In today's digital age, email is the backbone of business communication. It serves as the primary channel for exchanging information, making decisions, and maintaining records. Given its crucial role, safeguarding email communication through robust backup and security measures is essential. This article explores why email backup and security are vital for your business and provides practical steps to implement them effectively.
The Critical Role of Email in Business
Emails contain sensitive information, including contracts, financial data, personal information, and strategic plans. The loss or compromise of such data can lead to severe consequences, such as financial loss, reputational damage, and legal repercussions. Here are key reasons why securing and backing up email communication is critical:
Data Loss Prevention:
- Accidental Deletion: Employees might accidentally delete important emails.
- Hardware Failures: Servers or devices can fail, leading to data loss.
- Cyber Attacks: Ransomware and other cyber threats can result in data being encrypted or deleted.
Compliance and Legal Requirements:
- Many industries are subject to regulations requiring the preservation of communications for a specified period. Examples include GDPR, HIPAA, and FINRA.
- Failure to comply with these regulations can result in hefty fines and legal actions.
Business Continuity:
- In the event of a disaster, such as a cyber attack or natural catastrophe, having backups ensures that business operations can continue with minimal disruption.
Dispute Resolution:
- Email records are often needed to resolve disputes, providing a reliable source of evidence.
Implementing Effective Email Backup Solutions
To ensure the security and availability of email data, businesses should implement comprehensive email backup solutions. Here are key steps to consider:
- Regular Automated Backups: Set up automated backups to run at regular intervals. This ensures that the latest data is always saved and reduces the risk of data loss.
- Cloud-Based Backup Solutions: Use cloud-based services for email backup. These services offer scalability, off-site storage, and enhanced security features.
- Encryption: Ensure that backed-up data is encrypted both in transit and at rest. This protects the data from being intercepted or accessed by unauthorized parties.
- Redundancy: Implement redundancy in your backup strategy by storing copies in multiple locations. This provides an extra layer of protection in case one backup fails.
- Regular Testing: Periodically test your backup systems to ensure that data can be restored successfully. This practice helps identify and rectify any issues before they become critical.
Enhancing Email Security
In addition to backups, robust security measures are crucial to protect email communications from cyber threats. Here are essential security practices:
- Use Strong Passwords and Multi-Factor Authentication (MFA): Encourage the use of strong, unique passwords for email accounts and implement MFA to add an extra layer of security.
- Employee Training: Conduct regular training sessions to educate employees about phishing attacks, social engineering, and safe email practices.
- Email Filtering and Antivirus Solutions: Deploy advanced email filtering systems to detect and block spam, phishing attempts, and malware.
- Data Loss Prevention (DLP) Tools: Use DLP tools to monitor and protect sensitive information from being sent outside the organization.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure compliance with security policies and regulations.
Conclusion
In the digital landscape where email is indispensable for business operations, implementing robust email backup and security measures is not just a best practice but a necessity. By ensuring that emails are backed up regularly, encrypted, and protected against cyber threats, businesses can safeguard their critical communication channels, comply with legal requirements, and maintain continuity even in the face of disasters. Investing in email security and backup solutions is an investment in the longevity and integrity of your business.